- Use caution when you click links that you receive in messages from your friends on your social website. Treat links in messages on these sites as you would links in email messages.
- Don’t trust the sender information in an e-mail message. Even if the e-mail message appears to come from a sender that you know and trust, use the same precautions that you would use with any other e-mail message. Fraudsters can easily spoof the identity information in an e-mail message.
- Know what you’ve posted about yourself. A common way that hackers break into financial or other accounts is by clicking the “Forgot your password?” link on the account login page. To break into your account, they search for the answers to your security questions, such as your birthday, home town, high school class, or mother’s middle name. If the site allows, make up your own password questions, and don’t draw them from material anyone could find with a quick search.
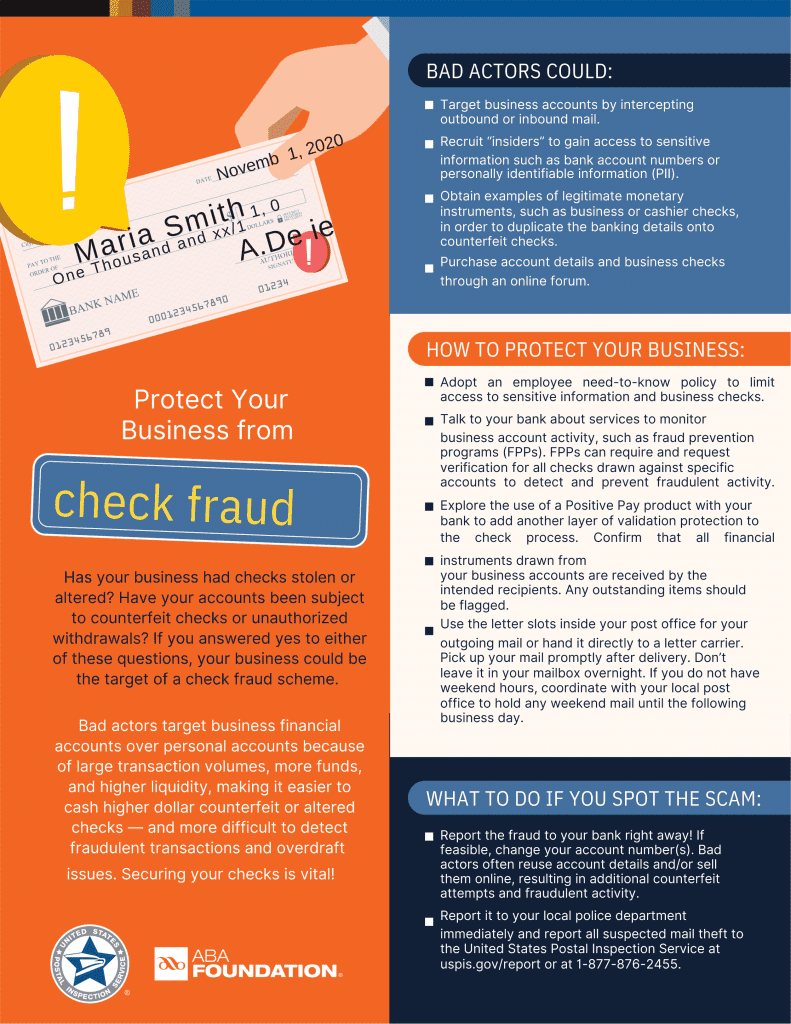
- Think twice before sharing personal information that would make you vulnerable. Social networking means opening up and sharing information online with others, but there’s some information you should never share online. Protecting yourself from sharing Too Much Information (TMI) can save you from identity theft and even protect your physical safety. So let’s start with the obvious – never share your social security number (including even just the last 4 digits), your birth date, home address or home phone number (although sharing your business phone is ok ). Of course, you should protect all of your passwords, PIN numbers, bank account, credit card information and never share the state where you were born as this information can be used to obtain your social security number and other identity information.
- Don’t trust that a message is really from who it says it’s from. Hackers can break into accounts and send messages that look like they’re from your friends, but aren’t. If you suspect that a message is fraudulent, use an alternate method to contact your friend to find out. This includes invitations to join new social networks.
- To avoid giving away email addresses of your friends, do not allow social networking services to scan your email address book. When you join a new social network, you might receive an offer to enter your email address and password to find out if your contacts are on the network. The site might use this information to send email messages to everyone in your contact list or even everyone you’ve ever sent an email message to with that email address. Social networking sites should explain that they’re going to do this, but some do not.
- Always type the address of your social networking site directly into your browser, use your personal bookmarks or official mobile apps. If you click a link to your site through email or another website, you might be entering your account name and password into a fake site where your personal information could be stolen. For more tips about how to avoid phishing scams, see Email and web scams: How to help protect yourself.
- Be selective about who you accept as a friend on a social network. Identity thieves might create fake profiles in order to get information from you. According to a recent survey by Harris Interactive, nearly 13 million Americans age 18+ who are on social networking sites will accept any social media connection request from a member of the opposite sex, regardless of whether or not they know that person. That lack of caution can be extremely costly. Most networking sites contain personal information. When you friend someone, you give them access to that information and that can be used by fraudsters.
- Choose your social network carefully. Evaluate the site that you plan to use and make sure you understand the privacy policy. Use privacy settings – The default settings on most social networking sites allow anyone to see your profile. Customize your settings to restrict access only to certain users. Despite the use of privacy settings, there is still a risk your information could be compromised so don’t post anything you wouldn’t want the public to see. Review your privacy settings periodically. Find out if the site monitors content that people post. You will be providing personal information to this website, so use the same criteria that you would to select a site where you enter your credit card.
- Assume that everything you put on a social networking site is permanent. Even if you can delete your account, anyone on the Internet can easily print photos or text or save images and videos to a computer.
- Be careful about installing extras on your site. Many social networking sites allow you to download third-party applications that let you do more with your personal page. Criminals sometimes use these applications to steal your personal information. To download and use third-party applications safely, take the same safety precautions that you take with any other program or file you download from the web. Use caution when deciding which apps to enable and take the same safety precautions you would take with any other program or file you download from the web. Modify your settings to limit the amount of information apps can access.
- Talk to your kids about social networking. If you’re a parent of children who use social networking sites.
- Search yourself. Do regular searches for yourself on a site such as Google. Know where you show up and what information is readily available online about you. Also, check out your social networking profiles as they appear to others and adjust your settings accordingly for privacy and security. You can also set up a Google alert with your name which could point to suspicious information and whether someone else is using your identity online.
- Customize privacy options. Social networking sites increasingly give users more control over their own privacy settings. Don’t assume you have to take whatever default settings the site gives you. Check out the settings, configuration and privacy sections to see what options you have to limit who and what groups can see various aspects of your personal information
- Limit work history details on LinkedIn: If you feel you need the added information to help in a job search, expand the details during the job hunting process and then cut back later after you have a position, leaving just enough information to entice recruiters to contact you with interesting new positions. LinkedIn also offers some capabilities to restrict information. You can close off access by others to your network of contacts, something you don’t have to share if you don’t want.
- Don’t trust, just verify. There are lots of reasons (most of them bad) why someone might impersonate or falsify an identity online. The question becomes, how can you verify that the page belongs to who you think it does before sharing too much information or clicking on links? Start by being on the lookout for anything unusual or out of the ordinary. If the content on the site doesn’t look like or sound like the person you know, avoid it. E-mail or call your friend to verify the site is legit. Let them know, too, if you think someone else is faking your friend’s identity online.
- Avoid accidentally sharing personal details. Social networking sites make it easy to let details slip you wouldn’t otherwise tell friends or strangers. Be aware of what information you put out there which others might use for nefarious purpose.
- Forget the popularity contest. Put a number on something and suddenly you have a competition. The person with the most “friends” isn’t necessarily the winner in social networking, unless of course you are running for president or you are in some type of recruiting, sales or media business. That’s just more people, including possibly strangers, who now have access to more of your information. It is best to only friend people who really are or have become your friends. Your personal information has less opportunity for misuse. If you do get an unsolicited invite to connect, check them out first and try to figure out why you know them or if you even do at all.
- Create a smaller social network. Bigger isn’t always better. There’s more to social networks than Instagram, Facebook and Twitter. Self forming communities often form around very narrow topics and these can easily get lost on the bigger sites. You may be better served creating a smaller, more focused network using tools aimed to help narrow or smaller groups. By narrowing your purpose and using tools appropriate for smaller groups, you can keep unwanted solicitations, invites to connect, applications and spam to a minimum. You’ll also find you build closer relationships with community members.
- Think twice before you use social networking sites at work. If you do, here are some ways to use that access more safely:
- Find out if your company has a policy about visiting certain Web sites using your corporate network.
- When you sign up for a social networking site, use your personal e-mail address, not your company e-mail address.
- Use caution when you click links that you receive in messages from your friends on your social networking site.
- Treat links in messages on these sites as you would links in e-mail messages.
- Be choosy about who you accept as a “friend” on a social network. Identity thieves may create fake profiles in order to glean information from you. This is known as social engineering.
- Be careful about the information you reveal about your workplace or company on your social networking site. (This is a good rule to follow for blogs too.)